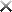C90-03Aテストエンジンはどのシステムに適用しますか?
オンラインテストエンジンは、WEBブラウザをベースとしたソフトウェアなので、Windows / Mac / Android / iOSなどをサポートできます。どんな電設備でも使用でき、自己ペースで練習できます。オンラインテストエンジンはオフラインの練習をサポートしていますが、前提条件は初めてインターネットで実行することです。
ソフトテストエンジンは、Java環境で運行するWindowsシステムに適用して、複数のコンピュータにインストールすることができます。
PDF版は、Adobe ReaderやFoxit Reader、Google Docsなどの読書ツールに読むことができます。
あなたのテストエンジンはどのように実行しますか?
あなたのPCにダウンロードしてインストールすると、SOA Certified Professional C90-03Aテスト問題を練習し、'練習試験'と '仮想試験'2つの異なるオプションを使用してあなたの質問と回答を確認することができます。
仮想試験 - 時間制限付きに試験問題で自分自身をテストします。
練習試験 - 試験問題を1つ1つレビューし、正解をビューします。
あなたはC90-03A試験参考書の更新をどのぐらいでリリースしていますか?
すべての試験参考書は常に更新されますが、固定日付には更新されません。弊社の専門チームは、試験のアップデートに十分の注意を払い、彼らは常にそれに応じてC90-03A試験内容をアップグレードします。
更新されたC90-03A試験参考書を得ることができ、取得方法?
はい、購入後に1年間の無料アップデートを享受できます。更新があれば、私たちのシステムは更新されたC90-03A試験参考書をあなたのメールボックスに自動的に送ります。
割引はありますか?
我々社は顧客にいくつかの割引を提供します。 特恵には制限はありません。 弊社のサイトで定期的にチェックしてクーポンを入手することができます。
返金するポリシーはありますか? 失敗した場合、どうすれば返金できますか?
はい。弊社はあなたが我々の練習問題を使用して試験に合格しないと全額返金を保証します。返金プロセスは非常に簡単です:購入日から60日以内に不合格成績書を弊社に送っていいです。弊社は成績書を確認した後で、返金を行います。お金は7日以内に支払い口座に戻ります。
Tech4Examはどんな試験参考書を提供していますか?
テストエンジン:C90-03A試験試験エンジンは、あなた自身のデバイスにダウンロードして運行できます。インタラクティブでシミュレートされた環境でテストを行います。
PDF(テストエンジンのコピー):内容はテストエンジンと同じで、印刷をサポートしています。
購入後、どれくらいC90-03A試験参考書を入手できますか?
あなたは5-10分以内にSOA Certified Professional C90-03A試験参考書を付くメールを受信します。そして即時ダウンロードして勉強します。購入後にC90-03A試験参考書を入手しないなら、すぐにメールでお問い合わせください。
SOA Certified Professional Cloud Technology Lab 認定 C90-03A 試験問題:
1. The cloud service owner of Cloud Service A is evaluating Clouds X, Y and Z to determine which cloud environment can offer the greatest level of reliability. All three clouds are geographically dispersed across three separate time zones. As a result, each cloud experiences usage peaks at different times. Based on the metrics provided, the greater the usage of a cloud, the lower its reliability. When the cloud service owner complains to Cloud Provider A (the owner of all three clouds) that none of the clouds provide an adequate level of reliability, Cloud Provider A suggests a solution that increases resiliency.
Which of the following statements accurately describes a solution that can be used to fulfill the resiliency requirements of Cloud Service A?
A) A cloud balancing solution is established, whereby a resource replication mechanism is implemented on each cloud. This allows Cloud Service A to be automatically replicated across cloud environments, thereby enabling each implementation of Cloud Service A to take the place of another, whenever failure conditions occur.
B) Redundant implementations of Cloud Service A are deployed in all three clouds. The failover system mechanism and a special type of automated scaling listener mechanism are implemented to establish a system whereby one redundant Cloud Service A implementation will automatically take over from another.
C) A failover system mechanism is implemented on Cloud X, which acts as the primary point of contact for cloud serviceconsumers. Upon failure conditions occurring, the Cloud Service A implementation on Cloud X automatically hands over control of current and future message requests from cloud service consumers to Cloud Y. Cloud Y retains control of cloud serviceconsumer communication until the next failure condition occurs, at which point it hands over control to Cloud Z. Finally, if a failure condition occurs in Cloud Z. control is handed back to Cloud X.
D) A cloud balancing solution is established, whereby an automated scaling listener mechanism is implemented on each cloud in such a way that every cloud can automatically scale out to another cloud. As a result, if reliability problems occur on any one cloud, the subsequent requests will be scaled out to another cloud in a manner that is transparent to cloud service consumers.
2. Organization A has been expanding and, as a result, is outgrowing the processing capacity of its on-premise Service A implementation. It is determined that this is due to usage thresholds of Service A and complex data processing limitations in Database A. The diagram depicts Organization A's current on-premise environment, where Service Consumers A. B and C attempt to access Service A at the same time. Service Consumer A successfully accesses Service A, which then successfully retrieves the requested data (1). Service Consumer B successfully accesses Service A, but due to the complex data structure, the request for the data times out and fails (2). Finally, Service Consumer C attempts to access Service A, but is rejected because Service A is unable to accept more concurrent requests.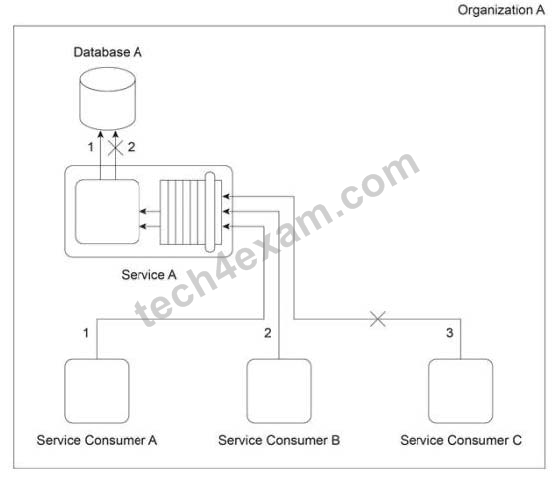
Organization A is required to continue using its on-premise Service A implementation, with the exception of Database A, which does not need to remain on-premise. Database A is dedicated to Service A and is comprised of relational data. Which of the following statements provides a solution that uses cloud-based IT resources to solve the performance limitations of Service A and Database A?
A) A failover system can be implemented in a hybrid architecture comprised of Organization A's existing on-premiseenvironment and a public cloud environment. The failover system would span both environments so that when Service A is unable to process request messages from Service Consumers A, B or C, the failover system can automatically route messages to a redundant implementation of Service A residing in the public cloud. Similarly, when Database Ais unable to process a data access request from Service the failover system can automatically route this request to a redundant implementation of Database A, also residing in the public cloud.
B) None of the above
C) The state management database and resource replication mechanisms can be implemented to establish redundantimplementations of Service A and Database A in both on-premise and cloud environments. Using resource replication, a cloud-based duplicate of Service A (Cloud Service A) will be established in a public cloud and will remain in synch with Service A via regular replication cycles. Using the resource replication mechanism together with the state management database mechanism allows for Database A to be dynamically replicated in an independent state management database that has redundant implementations in both on-premise and cloud environments. The state management database can be further optimized to support non-relational data to improve data access performance.
D) A cloud bursting solution can be implemented, whereby a redundant copy of Service A is implemented within a public cloud. This cloud-based, redundant implementation of Service A is referred to as Cloud Service A. A copy of Database A is also implemented within the cloud and both the on-premise and cloud-based copies of Database A are redesigned to be non-relational in order to improve data access performance. Service A continues to act as a first point of contact for Service Consumers A, B and An automated scaling listener is deployed so that when Service A's thresholds are met, requests are automatically routed to Cloud Service A.
質問と回答:
| 質問 # 1 正解: B | 質問 # 2 正解: D |


 弊社は製品に自信を持っており、面倒な製品を提供していません。
弊社は製品に自信を持っており、面倒な製品を提供していません。



 -山田**
-山田**